This posts provides an update on the cyber-physical risk assessment and airports’ requirements (WP2). To read the previous article on WP2, please follow THIS LINK.
The goal of this work package was to do the necessary analysis and preparation before diving into the more technical packages of this project. There were four main objectives:
- Perform a state-of-the-art analysis of security measures at the airports. This objective was led by AIA and included identifying critical assets within the airport environment, identifying known vulnerabilities already present in the airport, identifying safety and security requirements which must be abided by, and identifying the expected improvements in the security measures and how critical assets are handled. The output of this task resulted in two deliverables which were the foundation that the rest of the tasks in this work package built on, but also they set the stage for the rest of the project, identifying not only for the other tasks in this work package but also the project as a whole, to develop the SATIE solution in a way to protect the assets and mitigate potential vulnerabilities while staying within the confines of national and international regulations.
- Perform risk assessments of each threat scenario. The risk assessment was performed by NIS on each threat scenario (two at the Athens airport, one at the Milan airport, one at the Zagreb airport, and another only in the simulation environment). The risk assessment used the list of critical assets as well as any assets relevant to the threat scenario, and based on known vulnerabilities and known security measures, identified the riskiest assets (see Figure 1 with example data) and the vulnerabilities and threats which are the biggest sources of risk. This gave the airports, through an EU-restricted deliverable, further insight into their situation and potential security measures which could improve the risks.
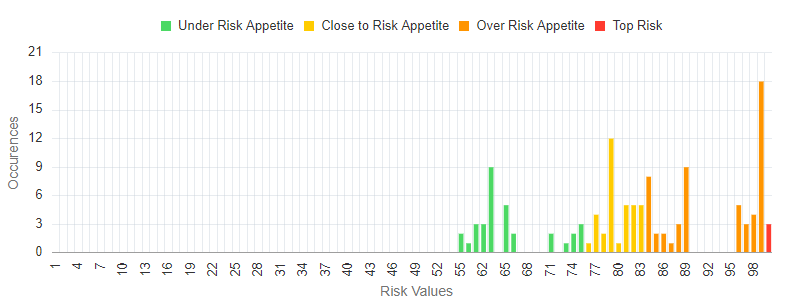
Figure 1: Example results of risks per asset, showing many assets with a risk above the risk appetite
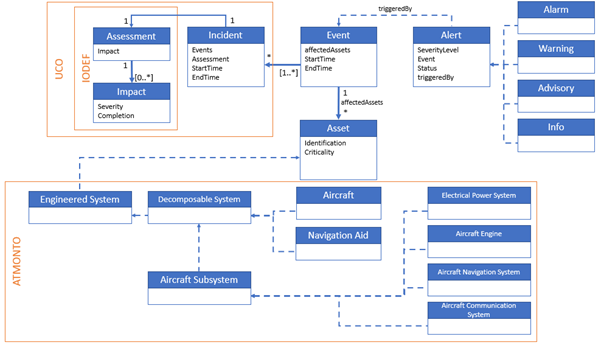
- Create a threat propagation model. Another way of evaluating threats within the airport environment is to model how the threats can propagate through the assets. Therefore, FHG created such a model based on asset interdependencies (physically, functionally, or digitally; see Figure 2) and using a library of known threats to those types of assets. By including information such as whether assets are in the same physical space as each other, or whether one asset (a database) contains another asset (passenger data), they could create rules to identify how a threat (e.g. “unauthorized access to software” of the database) could transform into another threat (e.g. “data tampering” of the passenger data). FHG wrote up the state of the threat propagation model as a deliverable but is continuing to work with the end-users, as part of task T5.1, to collect more information to make this model as accurate and useful as possible.
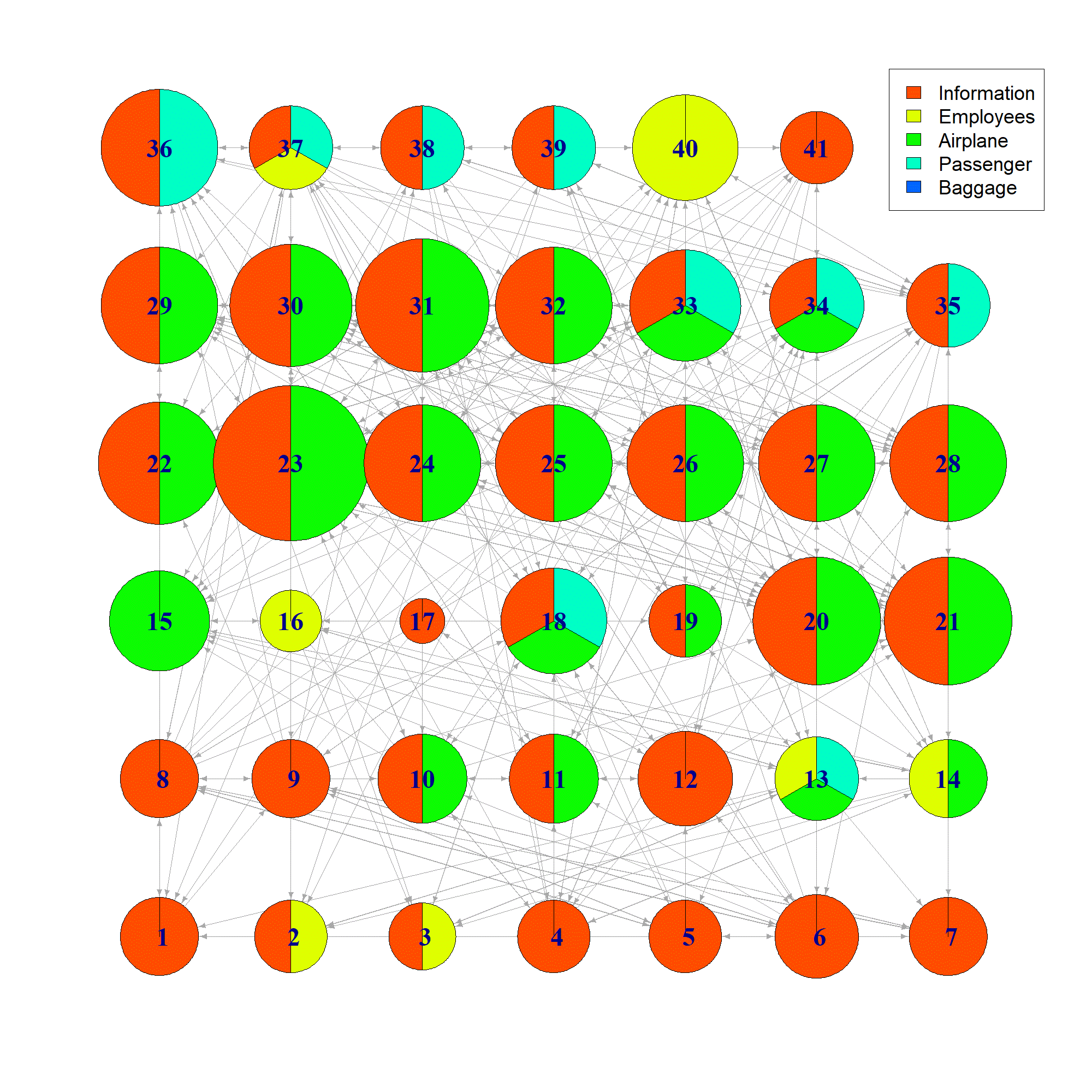
Figure 2: Network representation of the asset interdependencies in Scenario #5. Color represents the flow layer and the size represents the number of incoming dependencies.
- Develop a holistic security approach to implement based on the previous findings. Given that the goal of this project is to create a platform which can better detect, process, and alert threats in an airport, it is necessary to come up with a uniform security approach which would be followed. Therefore, KEM created one holistic approach, starting from the current practices and regulations applicable to each individual airport, which theoretically could be applied to other airports as well. The approach was based on a streamlined process of crisis management involving three phases: preparedness, response and recovery and mitigation (see Figure 3).
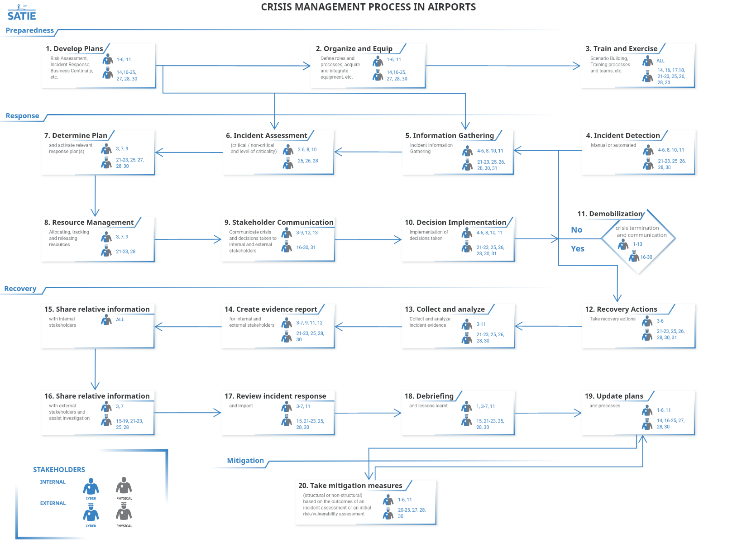
Figure 3: Common and holistic security and safety agenda
With these four objectives almost all completely met, the hands on work in the rest of the work packages of this project – such as deploying systems on the platform, making the systems communicate, deciding on what constitutes an alert – can proceed, having been informed of the as-is situation in the airports, where the weaknesses are, and what holistic approach to follow for the development of the platform.
Note: This output reflects the views only of the author(s), and the European Union cannot be held responsible for any use which may be made of the information contained therein. This project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 832969.